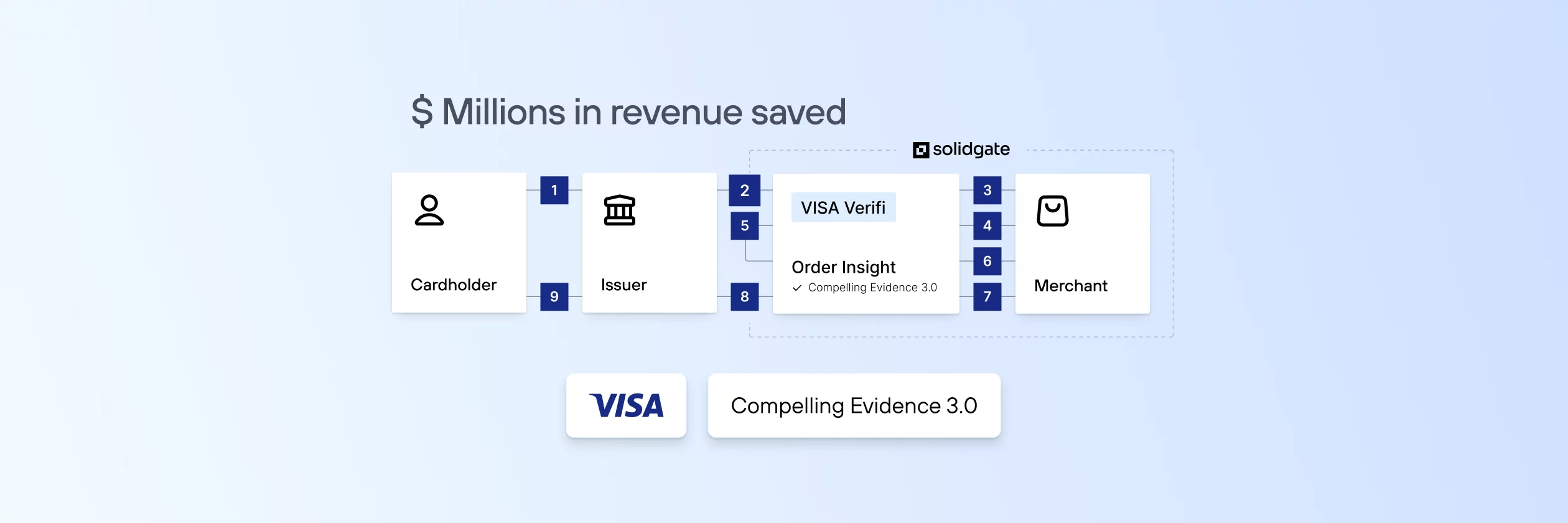
The Payment Card Industry Data Security Standard (PCI DSS) outlines crucial PCI DSS requirements that protect payment systems from credit card fraud. Meeting these standards is mandatory for merchants and payment providers handling cardholder data. This guide explains what PCI DSS entails, how to be PCI DSS compliant, the role of PCI DSS tokenization, and details on PCI DSS validation, including who has to validate PCI DSS compliance.
Table of Contents
What Are PCI DSS Requirements?
The Payment Card Industry Data Security Standards (PCI DSS) have several essential requirements for payment systems to protect against credit card fraud. Some key provisions include:
- Building and maintaining a secure network: This includes installing and maintaining a firewall configuration to protect cardholder data.
- Protecting cardholder data: This includes protecting stored cardholder data, encrypting the transmission of cardholder data across open, public networks, and regularly monitoring and testing networks.
- Maintaining a vulnerability management program: This includes regularly identifying and assessing vulnerabilities in systems and networks and implementing a process for applying security patches and updates.
- Implementing strong access control measures: This includes restricting access to cardholder data to only those who need to know and regularly monitoring and testing access controls.
- Regularly monitoring and testing networks: This includes regularly monitoring and testing networks to detect and respond to security incidents.
- Maintaining an information security policy: This includes creating, maintaining, and disseminating an information security policy that is regularly reviewed and updated.
- Managing service providers: This includes ensuring that any third-party service providers that handle cardholder data are also PCI DSS compliant.
Regularly reporting to the payment brands: This includes submitting regular compliance reports to the payment brands to demonstrate ongoing compliance with the PCI DSS.
Solidgate is compliant with PCI DSS, which means that it follows the security standards set by the major credit card companies to protect against credit card fraud and ensure the security of customer data.
Integration Method and PCI DSS Requirements
There are several methods for integrating payment systems with a merchant’s website or application, and each method has its implications for PCI compliance. List of PCI DSS Requirements:
Requirement 1: Install and maintain a firewall configuration to protect cardholder data
When storing credit/debit card data, you must protect it via a hardware and software firewall. To configure your firewall, you first need to establish security settings for each switch port. Then you need to create firewall rules, including the types of traffic allowed in and out of your network.
Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters
To enhance the security of your network, it is essential to change all passwords and usernames for administrator accounts. Passwords should be randomly generated, sufficiently long, and feature a mixture of letters, numbers, and symbols.
Requirement 3: Protect stored cardholder data
Cardholder data needs to be stored so that even if hackers bypass your firewall and get into your network, they can’t access readable data. This is achieved through a combination of encryption, hashing, truncation, and masking.
Requirement 4: Encrypt transmission of cardholder data across open, public networks
Whenever cardholder data is being sent and received across open public networks, it must be encrypted. This ensures that even if it is intercepted by a 3rd party, they can’t access usable data like card numbers, expiry dates, and CVVs.
Requirement 5: Use and regularly update anti-virus software or programs
Cybercriminals regularly gain access to networks and sensitive data by infecting an employee’s device with malware, which is often done remotely by sending nefarious links and attachments via messaging apps or email. Malware attacks can be prevented and quickly neutralized by installing anti-virus software on all devices connected to the network.
Requirement 6: Develop and maintain secure systems and applications
To keep the network secure, you must regularly update and install security patches. These patches are vendor-provided and quickly plug any vulnerabilities that hackers exploit.
Requirement 7: Restrict access to cardholder data by business need to know
To reduce the risk of inside attacks or a single compromised device causing cardholder data to be leaked, as few people as possible should have access to critical data. Only authorized personnel whose job responsibility involves cardholder data should have access.
Requirement 8: Assign a unique ID to each person with computer access
Before a user can access the network, they should be easily identifiable by a unique ID. This is so you can track users’ actions and quickly identify the source of any attacks.
Requirement 9: Restrict physical access to cardholder data
Cardholder data doesn’t just need to be digitally protected. You also need to protect criminals from physically stealing cardholder data by keeping track of device inventory, restricting certain physical areas where sensitive data is stored, and having a visitor log.
Requirement 10: Track and monitor all access to network resources and cardholder data
To quickly identify how, when, and where cardholder data was compromised, it is imperative that you track and log all users’ access to the network, including time stamps and user IDs.
Requirement 11: Regularly test security systems and processes
While your security system might theoretically work, you don’t know its true effectiveness until you fully test it. It is best practice to perform regular internal and external network vulnerability scans every 3 months and conduct network penetration tests yearly.
Requirement 12: Maintain a policy that addresses information security for all personnel
The information security policy must clearly explain the role and responsibilities that everyone in the company has in protecting against a cyber attack, and the policy must be updated annually. Companies need to create a formal training program, and employees need to undergo background checks.
Direct Integration
This method integrates the payment system directly with the merchant’s website or application. In this case, the merchant is responsible for ensuring that the payment system and their website or application are PCI-compliant.
Hosted Payment Page
This method involves redirecting the customer to a hosted payment page for the payment process. In this case, the merchant is not responsible for ensuring that the payment system is PCI-compliant. However, they are still responsible for ensuring that the customer’s personal and payment information is securely transmitted to the hosted payment page.
PCI DSS Tokenization
This method involves replacing sensitive cardholder data with a unique token, which can then be used for future transactions without storing or transmitting sensitive cardholder data. In this case, the merchant is not responsible for ensuring that the payment system is PCI-compliant. However, they are still responsible for ensuring that the tokenization process is secure and that the tokens are appropriately protected.
Payment Gateway Integration
This method involves using a payment gateway to handle the payment process. The payment gateway is typically PCI compliant, so the merchant is not responsible for ensuring that the payment system is PCI compliant. However, they are still responsible for ensuring that the customer’s personal and payment information is securely transmitted to the payment gateway.
In all cases, ensuring that the payment system used is PCI-compliant and that the integration method chosen is secure and meets industry standards is essential.
PCI DSS Validation
PCI DSS validation is the process of demonstrating compliance with the Payment Card Industry Data Security Standards (PCI DSS). The PCI Security Standards Council (PCI SSC) has established four levels of validation based on the number of transactions a merchant processes per year.
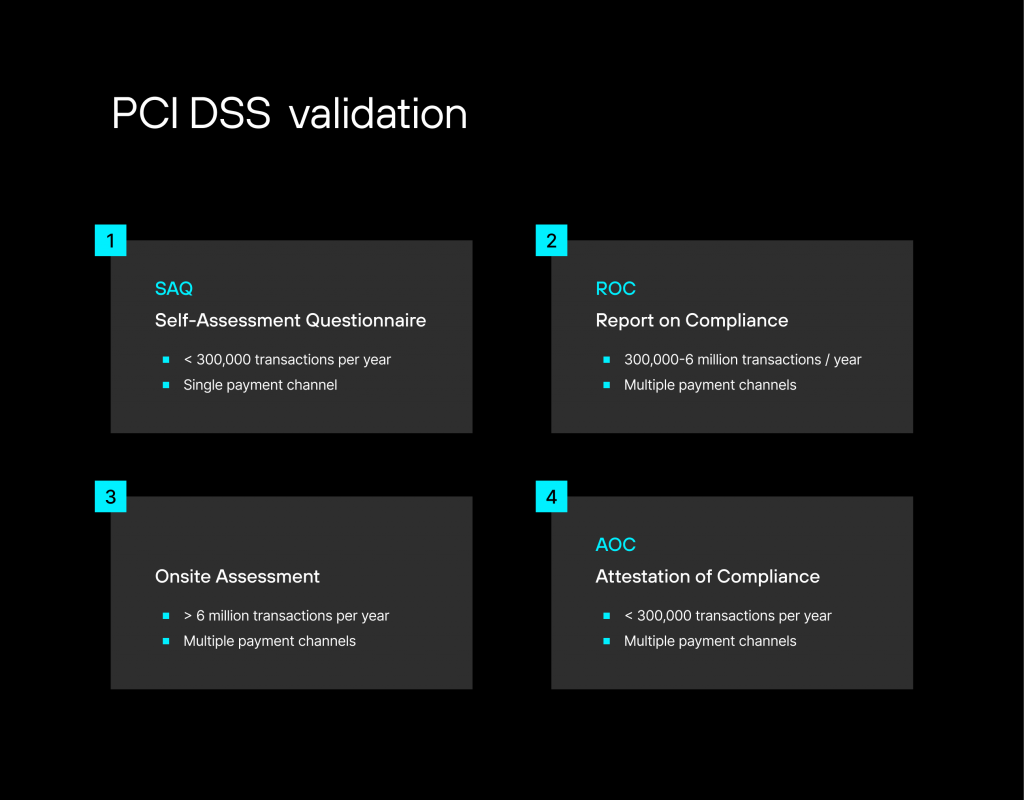
- Self-Assessment Questionnaire (SAQ): This validation level is for merchants who process fewer than 300,000 transactions per year and use only a single payment channel (such as a website or mail-order/telephone-order system). These merchants must complete a self-assessment questionnaire (SAQ) to demonstrate compliance with the PCI DSS.
- Report on Compliance (ROC): This validation level is for merchants who process between 300,000 and 6 million transactions per year and use multiple payment channels. These merchants must complete a Report on Compliance (ROC) that is reviewed and verified by a Qualified Security Assessor (QSA).
- Onsite Assessment: This validation level is for merchants who process over 6 million transactions per year and use multiple payment channels. These merchants must have an on-site assessment conducted by a QSA to demonstrate compliance with the PCI DSS.
- Attestation of Compliance (AOC): This validation level is for merchants who process fewer than 300,000 transactions per year and use multiple payment channels. These merchants must complete an Attestation of Compliance (AOC), which is reviewed and verified by a Qualified Security Assessor (QSA).
It’s important to note that PCI DSS compliance is an ongoing process, not a one-time validation. Merchants must regularly review and update their security measures to ensure they remain compliant with the PCI DSS.
Achieving Compliance through Solidgate
Solidgate, as a payment gateway company, offers a platform to merchants to securely accept and process credit card payments and provides various tools and services to help merchants achieve and maintain PCI DSS compliance. Some ways Solidgate can help merchants achieve compliance include:
PCI DSS-Compliant Infrastructure
Solidgate’s platform is built on a PCI DSS-compliant infrastructure, which means it follows the security standards set by the major credit card companies to protect against credit card fraud and ensure the security of customer data.
Tokenization
Solidgate provides tokenization services, which involve replacing sensitive cardholder data with a unique token. The token can then be used for future transactions without storing or transmitting sensitive cardholder data. This helps merchants reduce their PCI DSS scope and compliance burden.
Secure Payment Gateway
Solidgate provides a secure payment gateway that encrypts and transmits customer data to the merchant’s payment processor, which reduces the merchant’s responsibility for protecting customer data.
Compliance Support
Solidgate provides support and guidance to merchants in understanding and meeting the requirements of the PCI DSS, including completing self-assessment questionnaires and providing documentation and evidence to demonstrate compliance.
Regular Security Updates and Monitoring
Solidgate continuously monitors and updates its security measures to maintain compliance with the PCI DSS and protect customer data.
PCI DSS-Certified Partners
Solidgate works with certified partners such as PCI DSS QSA, PA-DSS, and PCI-DSS-certified Payment Service Providers (PSPs) to ensure that the merchants comply with industry standards.
By choosing Solidgate’s platform, merchants can focus on their core business while ensuring that their customers’ payment data is secure and protected.
How is PCI Compliance Validated with Solidgate?
In Solidgate, PCI compliance is validated through a combination of self-assessment and third-party assessment. The process of validation generally includes the following steps:
- Self-assessment: Solidgate conducts regular self-assessments to ensure that its platform and infrastructure comply with the Payment Card Industry Data Security Standards (PCI DSS). This typically includes a review of policies, procedures, and controls related to security, as well as regular testing and monitoring of the platform.
- Third-party assessment: Solidgate engages a Qualified Security Assessor (QSA) to independently evaluate the platform and infrastructure to verify compliance with the PCI DSS. This typically includes an on-site assessment of the platform and infrastructure, as well as a review of policies, procedures, and controls related to security.
- Reporting: Solidgate submits regular compliance reports to the payment brands to demonstrate ongoing compliance with the PCI DSS.
- Ongoing compliance: Solidgate continuously monitors and updates its security measures to maintain compliance with the PCI DSS and protect customer data.
- Attestation of Compliance (AOC): Solidgate provides Attestation of Compliance (AOC), which is reviewed and verified by a Qualified Security Assessor (QSA) to merchants who process fewer than 300,000 transactions per year and use multiple payment channels.
It’s important to note that PCI DSS compliance is an ongoing process, not a one-time validation. Solidgate must regularly review and update its security measures to ensure it complies with the PCI DSS.
Also, it is crucial for merchants to ensure that they are using a PCI DSS-compliant payment gateway and to work with the payment gateway to understand and meet the requirements of the PCI DSS.
Reporting a Non-Compliant Payment Provider
If you suspect that a payment provider is not abiding by the PCI DSS standards, you can file a complaint with the payment provider and/or the relevant credit card brand.
Complain to the Payment Provider
You can contact the payment provider’s customer service department and raise your concerns about their compliance with the PCI DSS. Provide any relevant information or evidence you may have to support your complaint. The payment provider is required to investigate and respond to your complaint.
Complain to the Credit Card Brand
You can also contact the relevant credit card brand (Visa, MasterCard, American Express, Discover, and JCB) and file a complaint about the payment provider’s compliance with the PCI DSS. The credit card brand will investigate your complaint and take appropriate action if it finds that the payment provider does not comply with the standards.
File a Complaint with the PCI SSC
You can also file a complaint with the PCI SSC (Payment Card Industry Security Standards Council) if you suspect that a payment provider does not comply with the PCI DSS. The PCI SSC will investigate your complaint and take appropriate action, including revoking the payment provider’s compliance certification, imposing fines and penalties, and even terminating the merchant agreement.
It’s important to note that the PCI SSC does not have the authority to enforce compliance with the PCI DSS. Still, they can revoke a merchant’s PCI DSS certification and issue fines to the QSA (Qualified Security Assessor) that issued the certification.
In summary, if you suspect that a payment provider is not abiding by the PCI DSS standards, you can file a complaint with the payment provider, the relevant credit card brand, and the PCI SSC. They will investigate your complaint and take appropriate action if they find that the payment provider does not comply with the standards.
How to Be PCI DSS Compliant: FAQs
Can you check in a database if a payment provider complies with PCI DSS?
There is no public database that lists all payment providers that are PCI DSS compliant. The PCI SSC (Payment Card Industry Security Standards Council) maintains a list of companies authorized to perform PCI DSS assessments and issue certificates of compliance. Still, it does not provide a list of all compliant organizations.
However, it is possible to check whether a payment provider is PCI DSS compliant by asking them for their PCI DSS certificate of compliance or their report on compliance (ROC). This certificate or report will indicate whether the provider has been assessed and found to be compliant with the standard.
Organizations should also be aware that a certificate of compliance does not guarantee that a provider is fully compliant at all times, as a successful assessment only indicates that the provider was compliant at the time of the evaluation.
Why is it so hard to meet the PCI DSS standard?
Meeting the PCI DSS standard can be challenging for several reasons:
- The standard’s complexity: The standard includes many requirements that cover a wide range of security controls and processes, making it difficult to understand and implement them all.
- Constant changes in technology: As technology evolves, new security risks emerge, and the standard must be updated to address them. This can make it difficult for organizations to keep up with the latest requirements.
- Difficulty in maintaining compliance: Organizations must maintain compliance with the standard continuously, which can be difficult as security threats and vulnerabilities constantly change.
- High costs: Implementing and maintaining compliance with the standard can be expensive. Organizations may need to invest in new technology and software or hire additional staff to meet the requirements.
- Human error: People can make mistakes, forget to follow security protocols, or ignore security warnings, leading to data breaches and non-compliance with the standard.
- Lack of expertise: Some companies may need more in-house expertise to understand and implement the standard, making it challenging to meet the requirements.
Is it possible to negotiate a PCI DSS certificate?
No, it is not possible to negotiate a PCI DSS certificate. PCI DSS is a set of security standards established by the major credit card brands (Visa, Mastercard, American Express, Discover, and JCB) to protect against credit card fraud.
Compliance with these standards is mandatory for any organization that accepts, processes, stores, or transmits credit card information.
The PCI DSS certification process is rigorous and includes a self-assessment questionnaire, an on-site assessment, and an annual report on compliance (ROC).
The certification process is conducted by Qualified Security Assessors (QSAs), independent auditors certified by the Payment Card Industry Security Standards Council (PCI SSC).
Organizations that do not meet the requirements will not be able to receive a PCI DSS certification.
While it’s not possible to negotiate a PCI DSS certificate, organizations can work with a QSA to understand the requirements and identify any gaps in their current security controls. They can then address these gaps and improve their compliance posture.
Who has to validate PCI DSS compliance?
Validation of PCI DSS compliance depends on the merchant’s annual transaction volume and payment channels. Smaller merchants often self-validate using a Self-Assessment Questionnaire (SAQ). In comparison, larger merchants require validation by a Qualified Security Assessor (QSA) through a Report on Compliance (ROC) or onsite audits. All merchants must regularly validate compliance to maintain PCI DSS standards.
Is it possible for a payment service provider to perform processing without complying with PCI DSS?
A payment provider can only perform processing with PCI DSS compliance. Compliance with the Payment Card Industry Data Security Standard (PCI DSS) is mandatory for any organization that accepts, processes, stores, or transmits credit card information.
If a payment provider is non-compliant with the PCI DSS, it will be prohibited from processing credit card transactions until they have taken the necessary steps to address the non-compliance issues and demonstrate compliance.
Non-compliance can also result in fines, penalties, and even termination of the merchant agreement.
What is the risk for the payment service provider that you will be caught not complying with PCI DSS?
The risk for a payment provider of being caught for non-compliance with the PCI DSS can be significant. Non-compliance with the standard can lead to costly data breaches and reputational damage.
If a data breach occurs and it is discovered that the payment provider was not in compliance with the PCI DSS, they may be subject to significant fines and penalties.
Credit card brands can also impose additional fines and penalties and even terminate a merchant agreement if they are non-compliant with the standard.
Additionally, a non-compliant payment provider may face legal action from customers who have compromised their personal and financial information due to a data breach. This can result in substantial financial losses and damage the company’s reputation.
Furthermore, not being compliant with the standard could also lead to a loss of customers’ trust and a potential loss of business with other merchants that don’t want to risk working with a non-compliant payment provider.
In summary, the risk for a payment provider of being caught for non-compliance with the PCI DSS is significant, as non-compliance can lead to costly data breaches, fines, penalties, legal action, and reputational damage.
Who should initiate verification of a payment provider’s compliance with PCI DSS?
The payment provider should initiate PCI DSS compliance verification, as they ensure compliance with the standard. Credit card brands and acquirers also conduct regular compliance reviews, monitoring, and investigations to detect any potential non-compliance.
It’s important to note that compliance with the PCI DSS standard is an ongoing process, and payment providers are required to maintain compliance on an ongoing basis. This includes regularly reviewing and updating their security controls and procedures to address new threats and vulnerabilities.
Ready to Secure Your Payment Processing?
Partner with Solidgate to ensure your payment systems meet the latest PCI DSS compliance requirements. Contact us today to learn how we can help you achieve and maintain PCI DSS compliance with secure, reliable payment solutions.